The world is still in a pioneering phase when it comes to traceability of commodities flowing in supply chains locally, regionally and globally. Much is written about this subject but very little is said. Authors of articles in contemporary literature think and write about the subject at a high level of abstraction and then miss the differentiators at the detail level.
One sees many different technologies and approaches being used in a variety of traceability systems. Most development engagements seem to focus on the identification of items, and on verification of origin. This is also referred to as the provenance of a product item. These solutions also invariably claim that they are created to provide the consumer with legitimate information about the products they buy. Such consumer-centric solutions increasingly claim to use the new blockchain protocol.
However, a recent development has been implemented as a value chain solution stretching across five consecutive roles in the cotton and cotton products value chain, aiming to still link up the remaining three to four roles to complete the journey from cotton farmers to consumers of cotton-based garments and fashion. This development stands out since it uses a new approach based on a fractal traceability solution protocol and a value chain architecture that is globally scalable and it is designed to primarily provide traceability and operations visibility to the participating organisations in the value chain and to facilitate data and information exchange.
And herein lies the nexus where we find ourselves in the field of traceability.
The way we talk about traceability and operations visibility
Right now there is no uniform or agreed framework of concepts, approaches and terminology to converse about new developments in traceability and operations visibility and to describe the trends that are emerging from all the diversity of approaches being followed. Any discussion of this kind, therefore, needs to first establish its own framework in order to calibrate the understanding of all participants in the discussion to a common set of concepts.
Traceability
Let’s start with the definition of traceability of products items throughout a value chain, from primary production (e.g. farmers if you think of food) through to retailers and then onwards to consumers. The global GS1 set of standards for commercial traceability lead us to define traceability as the monitoring and recording of physical item handling and service delivery events. If one considers an entire supply chain it means the monitoring and recording of physical item handling and service delivery events across all organisations that participate in the supply chain.
Physical item handling events, however, says nothing about the process and product attributes, or compliance to agreed standards and nothing about supply and demand dynamics. Hence one needs to conclude that traceability alone is not enough visibility on operations to enable an adequately informed view on how a product item moves through a supply chain, how it is produced, its grade and quality, the adherence of production processes to appropriate standards and best practices, and, very important for the trade, what is the committed demand against which production needs to be discounted.
Just as consumers have to trust retailers on the quality and provenance of products, retailers have to trust their supply chains. The trust of retailers in their supply chains, however, is based on the level of visibility, and the granularity of that visibility, they have across the entire supply chain.
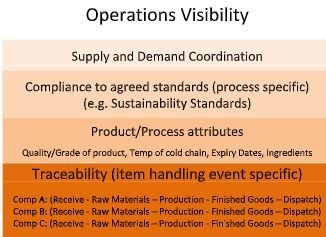
Figure 1: Schematic showing an example of a visibility stack required in a value chain, across all supply chains operating within, in order to adequately support operational and logistical risk management.
Visibility
The visibility stack that is required throughout supply chains is better explained in terms of the schematic diagramme below:
Traceability forms the backbone of visibility across a value chain. The other layers (for example the layers shown in Figure 1) represent complementary information that dovetails with the synchronicity of the traceability layer.
Integrity of traceability and operations visibility data
How do you know that the information in the blockchain or in the website that you access from the QR-code on the product item is trustworthy? You don’t! Unless there is an independent audit on the system, its data collection procedures and the validation of data and a certification process, it is not possible for a consumer or any other stakeholder to verify the integrity of the information.
The blockchain protocol, for example, is trustworthy in an information distribution role in the way it links information and encrypt it and distribute it securely, but it has no control over how, where from, and quality of the information that is put into the blockchain.
Quality of data and information in a traceability solution is controlled through a number of considerations.
These include, amongst others:
• Reducing human error through the elimination of clipboards and manual data capture, and
• Automation of data capture in physical item handling events through scanning of identifier codes, direct linking of weighbridges and platform scales to the servers that monitor and record these events, and
• Using the global GS1 standard for product item identification and marking
• Validating the identifier code of each item scanned against its previous handling event details as well as against the central identifier codes database, and
• Enforcing user-defined decision rules with respect to the sequence and location aspects of a physical item handling event as well as people access to the traceability platform, the information it contains and the authorisation to transact and change data values
It is therefore not only the system or its underlying technology that plays a role, but the entire solution stack contributes to the quality of data and information.
A solution stack is defined in terms of layers of value-add, for example the policy and business model as level one (the highest level), the associated business processes and procedures as level two, the hardware and software required to support these processes and procedures as level three, and the infrastructure required by the hardware and software to function optimally as level four.
Each of these layers has an impact on the quality of data and information. Validation of data is expected to be a standard procedure programmed into the traceability system. Verification of data and information is typically programmed into the traceability system as a procedure to, for example, match a product item identifier string with the previous item handling event and also with linkages to intermediate products in the value chain upstream in the supply chain.
Physical product verification can also be performed by stakeholders that have no direct access to the traceability system by scanning a QR-code or typing a human-readable code into an application linked to the relevant information that then takes the person to where the information resides in cyberspace.
Authentication is an additional feature in a traceability solution that operates independently from the product item identifier codes already mentioned.
Typically it is based on a natural unique feature of the product item such as chemical composition or added unique features such as micro-dots, artificial DNA strings, invisible ink, etc. Authentication, therefore, serves as an independent measure of origin, identity and even process, depending on which feature is being used. Authentication that is done on the basis of the product item identifier codes already mentioned simply adds another layer of verification, rather than an independent confirmation of provenance.
What does it mean for the future?
The world is frantically serious about finding solutions to make supply chains visible and to provide traceability behind product items. Large sums of investor and corporate funds are currently being spent on developing solutions based on different assumptions about human behaviour, a variety of business models and various technology approaches.
The following drivers are becoming evident:
• Need to share information between organisations participating in the same supply chains
• Communication of provenance information to consumers
• Need to enforce agreed and mandatory standards onto supply chains
• Enforcing food safety measures
• Providing for food security
• Competition between different supply chains for market share
• Efficiency gains both within and between organisations in a supply chain
Each of these drivers relies on different aspects of a traceability solution. For example, the vast majority of applications does not create and maintain a traceability audit trail across all the organisations in a supply chain. They simply collect information about origin, product attributes and any other information deemed useful for a specific kind of product, bring it together in a central place, link it to a QR-code (or similar) on a product item label and enable a consumer and other stakeholders to access the information by scanning the code on the label.
This is of course verification of a product item and not traceability. This kind of solution is much less capital intensive to develop, makes use extensively of smartphones, and is designed in a product-specific way around very specific production environments.
More reliability is achieved by replacing declarations by scanning of unique identifier codes and by using computers and tablet devices in production facilities rather than mobile phones.
The same basic approach is also followed with much higher security around access to and distribution of information by using the blockchain protocol. This, unfortunately, adds significantly higher costs to the overall solution. The blockchain bound information is safely fixed in its encrypted state, but also rigid in the sense that the same data cannot be interrogated under different sets of selection criteria like in a conventional database environment.These approaches to verification of product item provenance use a variety of approaches to data capture. Many rely, to a more or lesser extent, on a user making declarations of quality, origin, destination and the production process itself. These declarations are strung together with declarations from subsequent role players downstream in the supply chain in order to provide an overview of how product items progressed through a supply chain. Such approaches are also referred to as honesty models.
More reliability is achieved by replacing declarations by scanning of unique identifier codes and by using computers and tablet devices in production facilities rather than mobile phones.
Value chain shared services
A distinctly different kind of traceability is emerging through the fractal supply chain traceability protocol. This approach is designed as a value chain shared services infrastructure at a value chain level. All organisations in a supply chain link up to this infrastructure which creates and maintain a traceability audit trail across entire supply chains per product item instance, per batch, per organisation and per supply chain.
The solution is scalable through any length of a supply chain, through any number of supply chains within a value chain and through different levels of system architectures at a global level. The data capture in this approach is done primarily through the enterprise level systems currently in use in organisations, but can be augmented through the exposure of data capture functionality directly from the hosted service into the enterprise level. This approach is further characterised by creating a forensically hard traceability audit trail.
By specifying and harmonising each layer in the solution stack individually, the traceability and operations visibility solutions of the future will become very differentiated and specialised per product type per industry and per supply chain business model.
Many trade scenarios between a manufacturer and a retailer are done in the proven way of product type/quantity/batch accounting. By using the GS1 standard to identify and mark products and scanning technologies to automate data recording at item handling events most FMCG are subjected to this kind of visibility over the last drop of the supply chain. This approach, of course, excludes any visibility further upstream into the supply chain.Other exiting trends involve the integration of sensor data via IoT networks into the visibility stack of traceability and operations visibility platforms.
This is especially enabling in applications such as cold chain monitoring and recording. It means that a retailer can not only claim compliance to cold chain requirements, but it can proof that a specific product item has been exposed to specific cold chain temperatures during its journey through all the supply chain role players.
By specifying and harmonising each layer in the solution stack individually, the traceability and operations visibility solutions of the future will become very differentiated and specialised per product type per industry and per supply chain business model.







































